Abstract
A DLL side loading vulnerability was found in the VMware Host Guest Client Redirector, a component of VMware Tools. This issue can be exploited by luring a victim into opening a document from the attacker's share. An attacker can exploit this issue to execute arbitrary code with the privileges of the target user. This can potentially result in the attacker taking complete control of the affected system. If the WebDAV Mini-Redirector is enabled, it is possible to exploit this issue over the internet.
Tested versions
This issue was successfully verified on VMware Tools for Windows version 10.0.5 build 3228253.
See also
- CVE-2016-5330
- VMSA-2016-0010 - VMware product updates address multiple important security issues
Fix
This issue has been fixed in VMware Tools for Windows version 10.0.6.
Introduction
VMware Shared Folders is used to shared files between the guest & host operating system. VMware Host Guest Client Redirector is a component of VMware Tools that used to enabled Shared Folders in the guest operating system. Whenever a document is opened from a UNC path, the Client Redirector injects the DLL vmhgfs.dll (VMware HGFS Provider) into the application that is opening the document. The DLL is loaded from a relative path, the UNC path is also search when this DLL is loaded into the application. This allows for DLL hijacking, which can be used by an attacker to run arbitrary code with the privileges of the user that is opening the document from the share, potentially resulting in a full compromise of the affected system.
Details
When the Client Redirector loads the vmhgfs.dll DLL, it searches the Registry for its path. The path is stored in the Registry key HKLM\SYSTEM\ControlSet001\services\vmhgfs\networkprovider\ProviderPath. A relative path is used, which causes Windows to search for the DLL using the Dynamic-Link Library Search Order - including the current working directory.
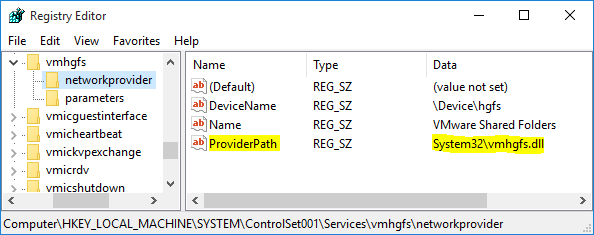 Figure 1: relative
Figure 1: relative vmhgfs.dll path
An attacker can exploit this issue by creating a network share (SMB or WebDAV) containing a System32 folder with a specially crafted vmhgfs.dll DLL. Luring a victim into opening a normal document (eg, DOCX, PDF) from the root folder of this share will cause the Client Redirector to load the attacker's DLL into the application that is used to open the document. This can be used to run arbitrary code with the privileges of the user that is opening the document from the share, potentially resulting in a full compromise of the affected system. If the WebDAV Mini-Redirector is enabled, it is possible to exploit this issue over the internet.
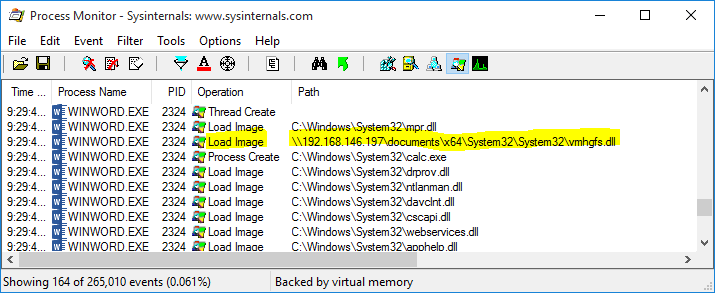 Figure 2:
Figure 2: vmhgfs.dll loaded from UNC path