Introduction
Last month we organized the Summer of Pwnage event, a Dutch community project. Its goal is to contribute to the security of popular, widely used open-source software projects in a fun and educational way. Or in layman's terms, gather a group of people to find vulnerabilities in WordPress and WordPress plugins, share the knowledge, and have fun while doing so.
How it started
The event itself started off as a joke while having a discussion about how Github's search function could be used to find vulnerabilities in open-source code. It didn't take long before this resulted in an unauthenticated PHP object injection vulnerability in a WordPress plugin. While the general belief is that such issues can be used to execute arbitrary code, often this is not the case as it depends on a number of conditions that have to be met. Curious as we are, we decided to find out if we could abuse the issue to execute arbitrary PHP code. As it turns out, this can be achieved with most (vulnerable) WordPress plugins :).
But quickly another question arose: we wondered how many of the Top X WordPress plugins are affected by similar issues. As the discussion progressed, somebody posed the idea to search for these issues together. One thing led to another and all of a sudden we had the challenge to organize Summer of Pwnage. Before we knew it the details were filled in and invitations were sent out for people to join in this joint effort!
Goal
Summer of Pwnage is a community project and its goal is to contribute to the security of popular, widely used open-source software projects in a fun and educational way. Summer of Pwnage is mainly targeted at (IT) students and people with little knowledge of software security - but surely everyone is most welcome to attend. Given the sheer number of WordPress plugins (at the time of writing this blog 46,057 plugins are readily accessible!) we figured that it would be feasible for people with little or no experience to find vulnerabilities in at least one of them. To help people get started and to share knowledge we also gave a number of talks. In addition, people could present their findings during the 'Pwn of the Week'.
The catch
During the event there were about 25 to 30 people actively participating in finding security vulnerabilities. A lot more people attended the meet-ups, and were present to learn new things. In the end 20 people submitted at least one pwn. At the last meetup we gathered one final time to rate all the submitted pwns. The participants were allowed to allocate a total of 5 points to their favorite pwn(s). After counting the total amount of points for all the submissions we found our lucky winner. Congratulations go out to Julien Rentrop with his winning pwn! You can find the advisory of the Cross-Site Scripting vulnerability he found in the Count per Day WordPress plugin here.

In total we received 118 unique submissions. We expected a lot of pwns, but even this was above our expectation :). At a certain point even the media started picking it up, for example:
- SC Magazine: WordPress Summer of Pwnage: 64 holes in 21 days
- Softpedia: Summer of Pwnage Event Yields 64 Security Bugs in WordPress Core and Plugins
Stats
Looking at the reported types of vulnerabilities, by far the most reported type is Cross-Site Scripting (66%). The majority of Cross-Site Scripting vulnerabilities were of the reflected type where the victim has to click on a malicious link or visit a malicious website (or advertisement). A fair share of them were stored though, and some of them even pre-auth.
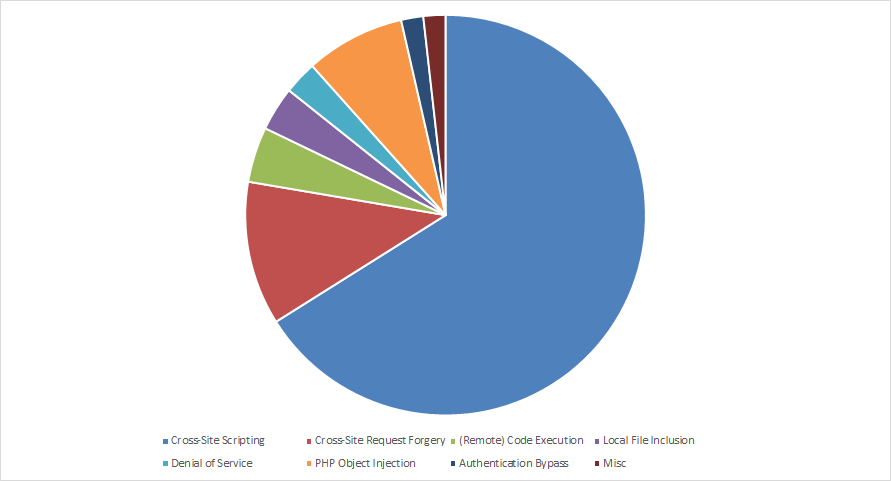
The runner-up is Cross-Site Request Forgery (12%). We didn't count the Cross-Site Scripting issues that are only exploitable through Cross-Site Request Forgery. Since these can fall into both categories we've counted them as Cross-Site Scripting.
The second runner-up is PHP Object injection (8%). The vulnerability type that ignited this whole vulnerability-finding-fest also made it into the top 3. Other notable vulnerability types are:
- Remote Code Execution (4%).
- Local File Inclusion (3%).
- Denial of Service (3%).
Looking at the submissions it seems that most people went for the low hanging fruit issues - grep still remains the king here.
Concluding
It is safe to say that the Summer of Pwnage was a great success. The number of findings exceeded far beyond our own expectations and we're really happy with the turnout. Of course some things can be improved, so the next event will be even more awesome - this is a learning event after all.
Will there be another Summer of Pwnage?
Most likely Yes. Summer '17 or maybe even this winter! We'll select a new target. If you have any good suggestions, let us know! Follow us on Twitter or subscribe to the newsletter for more info.
Where can I find the Summer of Pwnage presentations?
- Hypertext Prepwner: A beginner's guide to pwning PHP.
- Pwning the Bank: OWASP top 10 workshop.
- Pwning games: Cheaters, hookers and endbosses.
- Pwn of the Week: local file include.
- Hardening WordPress: A guide to stop or recover from a Pwn.
- Intermediate PHPwnage: Null bytes, timing and equality.
- Pwn automation: Integrating OWASP ZAP in your build pipeline.